
End-to-End Encryption in Writing Tools: How It Works
End-to-end encryption (E2EE) ensures your documents stay private and secure by encrypting data directly on your device and only decrypting it on the recipient's device. This approach prevents anyone - including service providers, hackers, or network intermediaries - from accessing your content. Here's what you need to know:
- How It Works: E2EE uses public and private keys for encryption and decryption. Data is encrypted into unreadable ciphertext before leaving your device and remains secure during transmission and storage.
- Benefits: Protects confidentiality, ensures data integrity, verifies sender authenticity, and prevents access even if servers are breached.
- Comparison: Unlike HTTPS, which only secures data in transit, E2EE keeps data encrypted at all times. Symmetric encryption, while faster, requires shared keys, making it less secure for communication.
- Writing Tools: Tools like Yomu AI use E2EE to protect sensitive documents, encrypting files locally and ensuring no one but you can access your content. Features like local AI processing further enhance privacy.
E2EE is a reliable choice for safeguarding sensitive information, especially for academics, researchers, and professionals. Using a plagiarism checker for academic papers alongside these security measures ensures both the integrity and privacy of your work. By keeping encryption keys in your control, it ensures your data stays private and secure at all times.
What Is End-to-End Encryption (E2EE) And How Does It Work? | E2EE Explained | Simplilearn
sbb-itb-1831901
How End-to-End Encryption Works
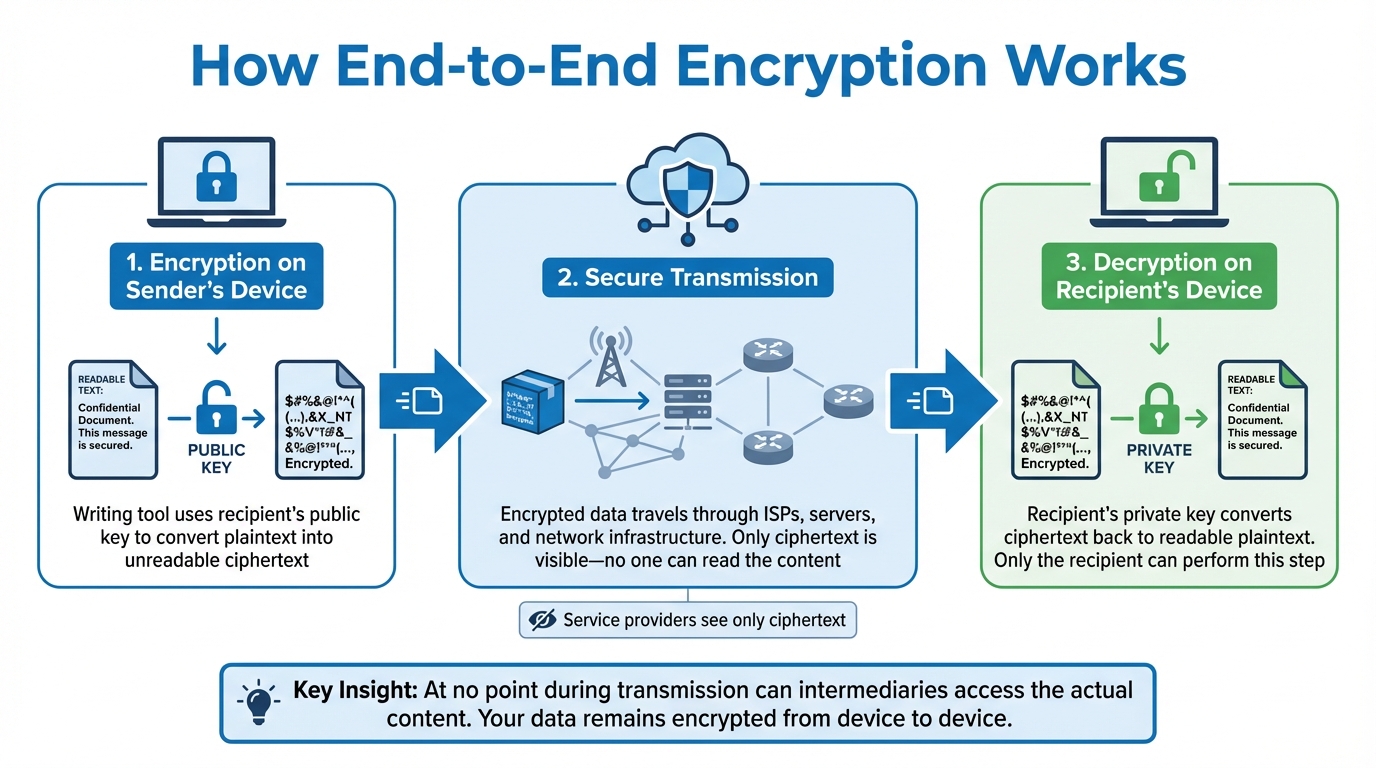
How End-to-End Encryption Works: 3-Stage Process from Device to Device
End-to-end encryption (E2EE) is a process that ensures your data remains private and secure throughout its journey - from the moment it leaves your device until it reaches its intended recipient. Here's how it works: your data is encrypted directly on your device, sent in its encrypted form, and only decrypted once it arrives at the recipient's device. This means that at no point during transmission can intermediaries access the actual content of your data.
The backbone of E2EE is asymmetric cryptography, which uses two mathematically connected keys: a public key and a private key. The public key is like a secure mailbox - anyone can drop a letter into it (encrypt data), but only you, with your private key, can unlock and read the letter (decrypt data). Sharing your public key doesn't compromise your private information, making this system both secure and practical. For instance, when you use an E2EE-enabled writing tool, your device encrypts your document before it’s uploaded to the cloud. What gets stored is ciphertext - an unreadable version of your data. Considering the global average cost of a data breach is $4.44 million and 81% of Americans worry about how their data is used, this level of security is crucial.
Key Generation and Asymmetric Cryptography
When you set up an E2EE-enabled tool, your device creates a pair of keys essential for encryption. The public key can be shared freely or stored on servers to allow others to encrypt messages meant for you. The private key, however, stays securely on your device.
"If you encode a message using a person's public key, they can decode it using their matching private key".
Asymmetric encryption does more than just secure data; it also authenticates the source of messages. This is achieved through digital signatures, which confirm that a message truly comes from the sender and hasn’t been altered in transit. To prevent eavesdropping or impersonation (man-in-the-middle attacks), many E2EE systems use fingerprint verification - unique strings or QR codes that confirm you're communicating with the right person.
While asymmetric encryption is powerful, it can be resource-intensive. That’s why modern E2EE tools use a hybrid approach: asymmetric encryption secures a session key, and this session key then enables faster symmetric encryption for the actual data. For example, Signal employs the "Double Ratchet" algorithm, which creates a new symmetric key for every message. This ensures that even if one key is compromised, past and future messages remain secure.
The Encryption, Transit, and Decryption Process
Once the keys are generated, the encryption process kicks off. This process unfolds in three key stages:
- Encryption on the sender’s device: The writing tool uses the recipient's public key to convert plaintext (readable text) into ciphertext (encrypted text) before the data leaves the sender’s device.
- Secure transmission: The encrypted data travels across the internet, passing through internet service providers, application servers, and other network infrastructure. Since the data is already encrypted, none of these intermediaries can access its content. Even the service provider only sees the ciphertext.
- Decryption on the recipient’s device: Once the ciphertext reaches its destination, the recipient’s private key is used to convert it back into readable plaintext. Only the recipient has the ability to perform this final step, ensuring that no one else - including the service provider or network administrators - can read the data.
It’s worth noting that this level of security comes with a trade-off: if you lose your private key and forget your password, your data might become permanently inaccessible unless you’ve set up a recovery phrase. This is a small price to pay for the peace of mind that your information remains safe from prying eyes.
End-to-End Encryption vs. Other Encryption Methods
Building on the technical details discussed earlier, it’s important to understand how end-to-end encryption (E2EE) stacks up against other encryption methods. Not all encryption approaches offer the same level of protection, and while E2EE is often considered the gold standard for privacy, other methods serve specific purposes and come with their own strengths and limitations. Knowing these differences can help you choose the right tools to keep your data safe. Here's how E2EE compares to HTTPS and symmetric encryption.
HTTPS (TLS) encrypts data while it’s being transmitted between your device and a server. However, once the data reaches the server, it’s decrypted, meaning the server has access to the content.
Symmetric encryption relies on a single key for both encrypting and decrypting data. This method is incredibly fast, making it ideal for encrypting large files, entire disk drives, or databases. The downside? Both parties need access to the same key, creating a potential vulnerability if the key is intercepted . Because of this, symmetric encryption is better suited for local data protection rather than secure communication across networks.
The critical difference lies in how far the encryption extends. HTTPS protects data only until it reaches the server, and symmetric encryption depends on securely sharing a single key. In contrast, E2EE ensures that only the sender and recipient can decrypt the data. Even if there are configuration errors or unauthorized access attempts, E2EE keeps the data safe. This is why E2EE is often seen as the most reliable option for safeguarding sensitive information.
Comparison Table: E2EE, HTTPS, and Symmetric Encryption
The table below highlights the key differences between E2EE, HTTPS, and symmetric encryption.
| Feature | End-to-End Encryption (E2EE) | HTTPS (TLS) | Symmetric Encryption |
|---|---|---|---|
| Security Scope | Device-to-device (in transit and at rest) | Device-to-server (transit only) | Data at rest or in transit |
| Key Management | User-controlled private keys | Provider-controlled keys | Single shared secret key |
| Access by Provider | Cannot access content | Can decrypt and read data | Anyone with the key can read |
| Speed/Efficiency | Slower (asymmetric handshake) | Fast | Very fast |
| Best For | Private documents, sensitive communications | Web browsing, standard cloud services | Full-disk encryption, databases |
| Recovery Risk | Data lost if key is lost | Provider can reset access | Data lost if key is lost |
This breakdown underscores why E2EE stands out as a top choice for protecting private communications and sensitive documents. While other methods are useful in specific scenarios, they don’t match the comprehensive security E2EE provides.
How Writing Tools Use End-to-End Encryption
Let’s dive into how writing tools implement end-to-end encryption (E2EE). This process involves multiple layers of protection that work together to ensure your documents stay secure - from the moment you start typing to when they’re stored or shared with others.
Client-Side Encryption for Document Security
E2EE in writing tools hinges on client-side encryption, meaning your documents are encrypted locally - right in your browser or app - before they ever leave your device. When you create a document, the tool generates a unique session key to encrypt both the content and metadata, such as the document’s title, creation date, and last modified timestamp.
Private keys are created and stored locally on your device, ensuring they’re never transmitted to the provider. This approach supports a zero-knowledge architecture, which means the company hosting the writing tool has no access to your document’s content. As Christian Pietsch from Digitalcourage e.V. explains:
"As an IT admin, I am glad that I cannot read the documents stored on my CryptPad server".
For collaboration, the document’s session key is encrypted using the public keys of all authorized collaborators. When multiple users edit a document simultaneously, encrypted updates are sent securely via WebSockets. Only those with the symmetric key can decrypt and apply these updates, ensuring that real-time collaboration happens without the server ever accessing the actual content.
Protecting Data in Transit and at Rest
Beyond client-side encryption, writing tools also secure your data as it moves across networks and while it’s stored. Since encryption occurs on your device before the data is uploaded, it remains encrypted throughout its entire journey and storage lifecycle. Even in the event of a server breach or an intercepted network, the data remains unreadable without your private key.
Some tools take it a step further by enabling link sharing through a "link key" embedded in the URL fragment (the part after the # symbol). Because browsers don’t send this fragment to the server, the link remains private between the people sharing it. However, there’s a trade-off: since the server can’t access your documents, features like server-side search indexing aren’t possible. Instead, E2EE tools handle search indexing directly on your device.
How Yomu AI Uses End-to-End Encryption
Yomu AI employs E2EE to safeguard academic documents throughout the writing process. Whether you’re drafting essays, research papers, or other academic work, your documents are encrypted on your device before being uploaded. This ensures your research, drafts, and final papers remain private - even when using AI-driven features like sentence autocomplete, paraphrasing, or summarization.
Yomu AI’s zero-knowledge system ensures that private keys never leave your device. This is especially critical for students and researchers handling unpublished work, sensitive thesis material, or original ideas that need protection before publication. To further enhance privacy, E2EE tools like Yomu AI prioritize "endpoint-local" processing, meaning the AI features run directly on your device rather than relying on cloud servers. This way, users can enjoy advanced writing assistance without compromising their privacy.
Additionally, Yomu AI’s zero-knowledge design ensures private keys stay securely on your device. If you lose your password, only a recovery key can restore access.
Common Encryption Algorithms Used in E2EE
End-to-end encryption (E2EE) systems rely on two key types of encryption algorithms: symmetric (single-key) and asymmetric (dual-key) encryption. Most modern E2EE systems, including those used in writing tools, combine these methods in a hybrid approach to balance security with performance.
AES (Advanced Encryption Standard)
AES is the go-to symmetric encryption algorithm, using a 256-bit key for both encrypting and decrypting data. It’s known for its speed and efficiency, making it ideal for protecting documents. According to Bitwarden:
"With proper implementation... and a strong encryption key, AES is considered unbreakable".
This algorithm is trusted to secure top-secret data for the U.S. government and is widely adopted by security agencies around the globe.
RSA (Rivest–Shamir–Adleman)
RSA is a cornerstone of asymmetric encryption. It employs a pair of keys - a public key for encryption and a private key for decryption. Its security comes from the mathematical challenge of prime factorization. While RSA is slower and more resource-intensive than AES, it excels in securely exchanging symmetric keys and creating digital signatures to authenticate senders.
Diffie-Hellman (DH)
Diffie-Hellman focuses on securely generating a shared secret over an insecure channel. Many modern systems incorporate DH into algorithms like the "Double Ratchet", which generates a fresh symmetric key for each message. Signal, for example, describes their implementation as:
"We wanted a ratchet that combines the best of both worlds: the optimal forward secrecy that a hash iteration ratchet like SCIMP provides, as well as the nice future secrecy properties that a DH ratchet like OTR provides".
This design ensures that even if one key is compromised, both past and future messages remain secure.
Hybrid Encryption in Writing Tools
Writing tools often combine AES with SHA-256-based HMAC to encrypt data while also verifying its integrity. This hybrid method forms the backbone of the robust client-side encryption techniques mentioned earlier, ensuring a high level of security for users' data. Together, these algorithms create a strong foundation for modern E2EE systems.
Conclusion
End-to-end encryption (E2EE) has emerged as the benchmark for safeguarding sensitive documents in writing tools, particularly for academic and professional users managing confidential research, unpublished manuscripts, or proprietary data. As highlighted by the UN Office of the High Commissioner on Human Rights:
"Strong encryption is essential to fundamental human liberties including free expression, the right to hold opinions, the right to privacy, and the right to assembly".
What sets E2EE apart is simple yet powerful: the decryption keys remain exclusively with you. Unlike standard HTTPS encryption, where service providers can access your data once it reaches their servers, E2EE ensures your documents stay encrypted both during storage and transmission. This means that even in the event of a server breach or external legal demands, only you and your chosen collaborators have access to your content.
For academics, this level of security is indispensable. Platforms like Yomu AI leverage E2EE to protect unpublished research, prevent unauthorized data access, and keep your drafts confidential. With over 100 million users benefiting from zero-access encryption principles, the technology has proven to be both reliable and scalable.
To enhance your security even further, opt for tools that process AI locally instead of relying on cloud-based services. Always enable opt-in settings for AI features to maintain control over your data and set up secure recovery options, such as recovery phrases, to prevent permanent data loss. By using robust encryption standards like AES-256 and RSA with proper key management, you can confidently protect your most sensitive work.
FAQs
How does end-to-end encryption keep my writing secure?
End-to-end encryption (E2EE) ensures your writing stays private by encrypting your data directly on your device and keeping it encrypted until it reaches its intended recipient. Essentially, your content is turned into unreadable code before it leaves your device, and only the recipient has the unique key to decode it. This means no one else - whether it's hackers, service providers, or even the platform itself - can access your work.
E2EE relies on cryptographic keys, typically involving a pair: a public key and a private key. The sender uses the recipient’s public key to encrypt the data, and only the recipient’s private key can decrypt it. This setup guarantees your writing remains confidential, even if it’s intercepted or stored on external servers. However, because the platform has no access to your encrypted data, losing your password or decryption keys could mean your data is unrecoverable. While this approach offers strong protection, it also places the responsibility of safeguarding your keys squarely in your hands.
How does end-to-end encryption differ from other encryption methods like HTTPS?
The key distinction between end-to-end encryption (E2EE) and other encryption methods, like HTTPS, lies in who has access to your data. With E2EE, encryption happens directly on your device, and only the intended recipient can decrypt the information. This ensures that no one else - whether it's a third party, hacker, or even the service provider - can view the unencrypted data.
In contrast, HTTPS protects data while it's being transmitted between your device and a server. However, once the data reaches the server, it gets decrypted, meaning the server (and potentially anyone with access to it) can view the information. While HTTPS is great for securing data during transit, it doesn't guarantee privacy from the service provider or others who might access the server. E2EE provides an added layer of security by ensuring that only the sender and recipient have the keys to unlock the data.
How can I keep my private key secure, and what should I do if I lose it?
To protect your private key, make sure to store it in a secure location, like an encrypted storage system or a hardware security device. Never share it with anyone, and avoid saving it on shared drives or unsecured devices where it might be vulnerable.
Losing your private key can have serious consequences. Without it, you’ll likely lose access to any encrypted data linked to that key, as it’s a crucial tool for decryption. Unfortunately, there’s usually no way to retrieve the data if the original key is lost. That’s why it’s so important to take every precaution to keep it safe.
